Scenario for Enterprise Single Sign on Solution
Sample Scenario:
Outline the steps for creating an enterprise single sign on solution to be used with enterprise applications such as Oracle E-Business Suite (EBS
Conduct Strategy Assessment of your company or agency’s Application Landscape, Enterprise Architecture and IT Security. The result will produce an Enterprise Application Road Map to Transformation. Portfolio rationalization efforts of your enterprise will be the framework for the Single Sign On (SSO) Implementation Plan. The following graphic depicts a high level approach that SIS would use for implementation of enterprise Single Sign On (SSO) capability at YOUR COMPANY.
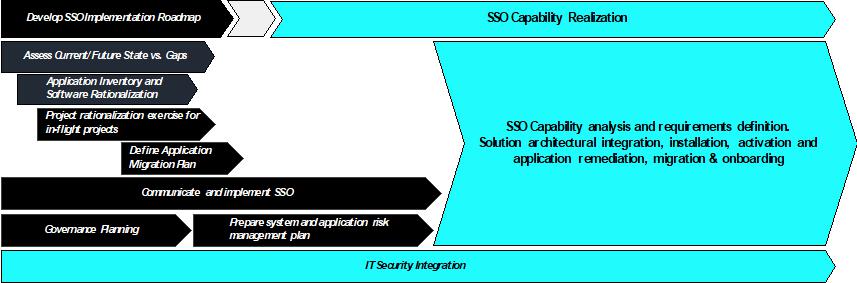
The following outline provides the high level approach steps for implementation of enterprise Single Sign On (SSO) capability at YOUR COMPANY.
1. Define the Scope of Single Sign On (SSO) requirements
-
Assess current state and define future state Application, Data and Systems
-
Identify and inventory current application portfolio and technologies
-
Develop SSO architectural model and IT Security integration plan
-
Develop prioritized list of requirements for SSO capability
2. Conduct a gap analysis on the enterprise architecture, application landscape and SSO solutions.
-
Using the outputs from Step 1 – compare to identify gaps
-
Identify integration with existing enterprise architecture and application architecture
-
Highlight critical architecture/system/process/capability gaps
-
Research, identify, select, source and acquire SSO solution that achieves desired capability requirements
3. Define process in which applications will be activated within the SSO environment
-
Develop roadmap for SSO solution implementation and integration plan
-
Establish priority and criteria for all projects to be active on SSO
-
Conduct project rationalization exercise for in-flight or active projects
-
Develop migration plan for all applications to be migrated to SSO environment
-
Deploy governance processes for SSO management
4. Conduct a thorough readiness review process for application onboarding to SSO environment
-
Stakeholder engagement
-
Data points and measurement methods for SSO
-
Level of organizational integration
-
Implement SSO Solution Integration Plan
An enterprise that supports more than 5,000 users can oftentimes provide 100’s of applications that support the mission critical business operations. These applications usually leverage various application and middleware technology to include J2EE, ASP.NET, PHP, Oracle Suites, Hyperion, and SAP to name a few. In addition, the applications utilize various flavors of both UNIX and Windows operating systems for hosting. Lastly, your company or agency must provide end point access to all client devices, which typically include Apple, Microsoft and sometimes Android devices. All of this technology requires identity, access and authorization control, but usually isn’t streamlined into a Single Sign-On (SSO) solution. As highlighted in figure 1, multiple authentication sources can exist for the various application technologies. This architecture results in an increase in the complexity of password management, as each may have a separate username or password for authentication. There is a major increase in security risk in this type of architecture. The result:
-
Utilization of “local” accounts to include administrative accounts
-
Users having elevated or not “least privileged” access
-
Lack of auditing capability
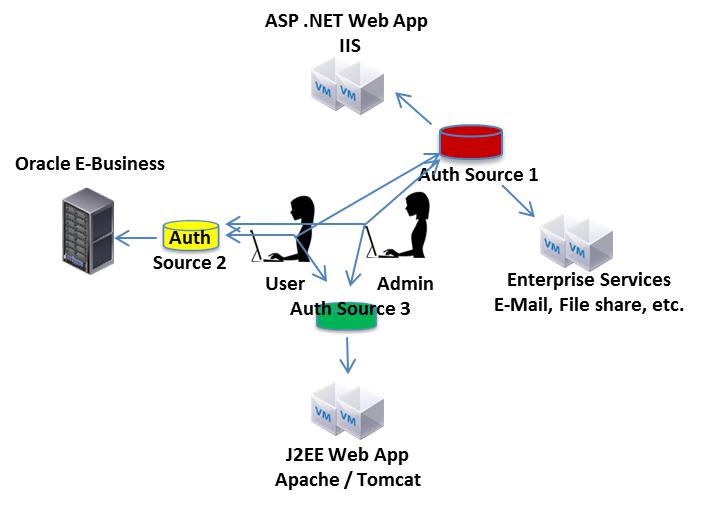
Figure 1 - Non-Single Sign-On Design
The resolution to the risk identified in Figure 1 is the implementation of a SSO technical solution that integrates with all of the services in the enterprise. In addition, a key component is formulating a role based access control (RBAC) process that will enforce using the SSO solution. As shown in Figure 2 a SSO solution will minimize the complexity of authentication and authorization, as well as support an efficient auditing and access control governance process.
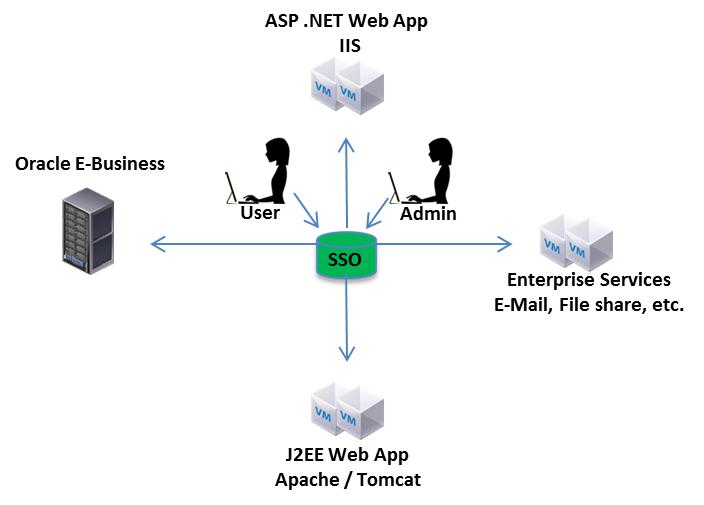
Figure 2 - Single Sign-On Solution
The level of effort for implementing a SSO solution depends on a combination of the different application and operating system technologies that are supported in the environment, current maturity of an enterprise access control process and the business unit motivation for transitioning from legacy access control methodologies. The resourcing for the high level approach is outlined in table 1. Any task identified that has already been completed will result in resource elimination or reduction from the level of effort.
Sample Performance Measures:
-
Number of test case errors
-
Number of revisions to plan
-
Number of documentation errors
-
Percent of problems uncovered before design release
SIS has implemented SSO solutions for the various application technologies mentioned both on premise and in the cloud.
Schedule a Free Consultation
We help global leaders with their organization's most critical issues and opportunities. Together, we create enduring change and results.

Super Efficient

Deeply Committed


